Confidential information stored in a hard drives are always a target of identity thieves because most people or organization knows nothing about data security. When organizations upgrade their computer, they often forget to do the security measures in making the files unrecoverable.
Normally formatting is a way to get rid of all the data in the HDD but this method doesn't make the files unrecoverable. It just makes room for free space, so your old files will be overwritten. This is where most business, companies, and organization fails. What they do is format the disk then they either send it to recycling centers or sell them to people.
Another mistake, which can compromise their data security is how people deals with broken disks. Did you know that malfunctioning disks still have files in them that can be recovered using straightforward techniques like using a file recovery CD or a more advance file recovery method like transferring a disk platter to another hard disk of the same make and model.
It is possible to wipe data in a disk. Wiping is a process wherein the erased file is overwritten several times, so the files will no longer be recovered. The wiping process is easy, but the result is unpredictable. Sometimes, no matter how many times a disk wiping is performed, a file recovery software will still be able to recover it.
A hard disk that contains personal information of customers can be recovered by thieves in which they can use to
That is why it is recommended to perform HDD destruction before throwing away hard disk drives. Before it is done, there are pointers to remember first:
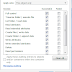
List of files in HDD which will be prone to identity theft and data breach: social security number
Financial records
Personal information (complete name, birthday, address) credit card numbers
Customer's database with a name, birthday, social security number, address, etc. medical records
Tax records
Trade secrets
Strategic business plans
Verify if the hard disk is fully functional or not working. A fully functional hard disk can benefit from disk wiping method the best solution to make wiping unrecoverable is to do several passes. 7 pass is not enough, and 35 passes are a sure way to remove data. Make sure to perform a disk verification procedure to verify if all files are unrecoverable.
Normally formatting is a way to get rid of all the data in the HDD but this method doesn't make the files unrecoverable. It just makes room for free space, so your old files will be overwritten. This is where most business, companies, and organization fails. What they do is format the disk then they either send it to recycling centers or sell them to people.
Another mistake, which can compromise their data security is how people deals with broken disks. Did you know that malfunctioning disks still have files in them that can be recovered using straightforward techniques like using a file recovery CD or a more advance file recovery method like transferring a disk platter to another hard disk of the same make and model.
It is possible to wipe data in a disk. Wiping is a process wherein the erased file is overwritten several times, so the files will no longer be recovered. The wiping process is easy, but the result is unpredictable. Sometimes, no matter how many times a disk wiping is performed, a file recovery software will still be able to recover it.
A hard disk that contains personal information of customers can be recovered by thieves in which they can use to
That is why it is recommended to perform HDD destruction before throwing away hard disk drives. Before it is done, there are pointers to remember first:
List of files in HDD which will be prone to identity theft and data breach: social security number
Financial records
Personal information (complete name, birthday, address) credit card numbers
Customer's database with a name, birthday, social security number, address, etc. medical records
Tax records
Trade secrets
Strategic business plans
Verify if the hard disk is fully functional or not working. A fully functional hard disk can benefit from disk wiping method the best solution to make wiping unrecoverable is to do several passes. 7 pass is not enough, and 35 passes are a sure way to remove data. Make sure to perform a disk verification procedure to verify if all files are unrecoverable.